LoRa Technology
An Open Standard to create your network.

Introduction
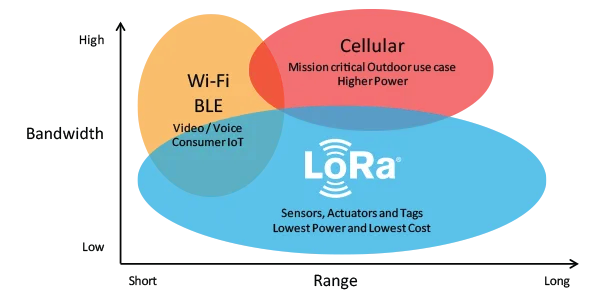
LoRa (short for long range) is an RF modulation technology for low-power, wide area networks (LPWANs).
Key features of LoRa®technology
- Long range: >15 km
- Low-power: 5-10 year expected battery lifetime
- Low-cost: from end-node sensor cost to upfront infrastructure investment
- Secure: with embedded end-to-end AES-128 encryption of data
- Geolocation: enables indoor/outdoor tracking without GPS
LoRa is purely a physical (PHY), or “bits” layer implementation.
LoRa transmits over license-free sub-gigahertz radio frequency bands like 169 MHz, 433 MHz, 868 MHz (Europe) and 915 MHz (North America).
LoRa uses a proprietary spread spectrum modulation that's like to a derivative of chirp spread spectrum (CSS) modulation.
The basic premise of spread spectrum is that each bit of information is encoded as multiple chirps. The value of Spreading Factor (SF) determines how many chirps are used to represent a symbol.
Bandwidth is the frequency range of the chirp signal used to carry the baseband data. Allowed values are 125, 250 and 500 kHz.
LoRa modulation also includes a variable error correction scheme that improves the robustness of the transmitted signal at the expense of redundancy.
We can define the nominal bit rate of the data signal as:
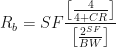
Where:
- SF = spreading factor (7..12)
- CR = code rate (1..4)
- BW = modulation bandwidth (Hz)
LoRaWAN
LoRaWAN™ defines the communication protocol and system architecture for the network while the LoRa® physical layer enables the long-range communication link.
LoRaWAN networks are deployed in a star-of-stars topology.
LoRaWAN Architecture
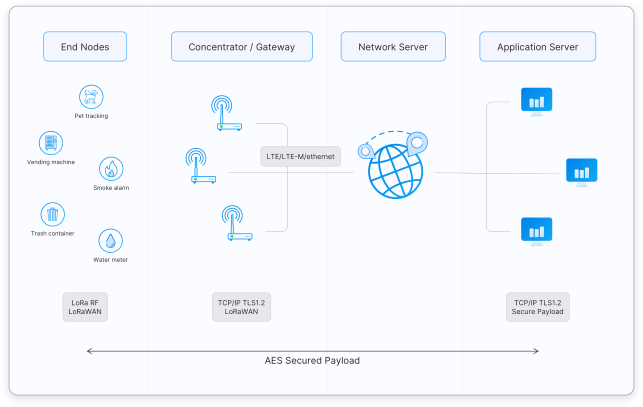
- End devices: A LoRaWAN end device can be a sensor, an actuator... They are often battery operated.
- Gateways: A gateway receives LoRa messages from end devices and simply forwards them to the LoRaWAN network server. Gateways are embedded with a multi-channel and multi-data rate radio-frequency device that can scan and detect packets on any of the active channels. Are often battery-powered.
- Network Server: The LoRaWAN Network Server is the brain and the controller of a LoRaWAN network. It guarantees a lot of features.
- Application Server: The Application Server takes care instead of receiving and analyzing the data sent by the nodes. It also generates all the application-layer downlink payloads and sends them to the connected end devices through the Network Server.
Device Classes
The LoRaWAN specification defines three device types: Class A, Class B, and Class C.
- Class A: When an uplink is sent to the server the device opens two small windows for any commands, if the server is not able to send a downlink in the two small windows, it will have to wait until the next uplink.
- Class B: In addition to the two Class A windows, Class B has an extra downlink window, which is opened at scheduled times.
- Class C: Extend Class A by keeping the receive windows open unless they are transmitting. Are often mains powered
Security Keys
LoRaWAN specifies three security keys:
NwkSKey (Network Session Key),
AppSKey (Application Session Keys) and AppKey (Application Key).
All keys have a length of 128 bits and 128-bit AES encryption algorithm is used,
similar to the algorithm used in the 802.15.4 standard.
When a device connects to the network (this is called a join or activation) an AppSKey and a NwkSKey are generated.
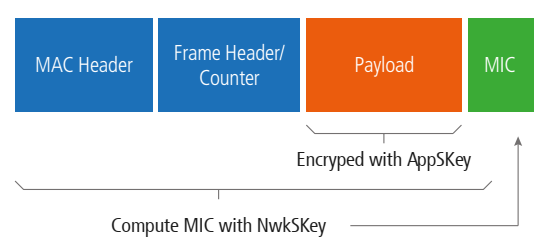
The NwkSkey is shared by both the end device and the network server to generate and verify the message integrity code (MIC).
The AppSKey is used for encryption and decryption of the payload, is only known by the device and by the application.
LoRaWAN specifies a number of identifiers for devices.
All end-devices have a 64-bit unique identifier called DevEUI (Device Identifier).
In addition, all communication is done using 32-bit device address (DevAddr).
AppEUI (Application Identifier) is another identifier which uniquely identifies the application provider of the end-device.
Activation
LoRaWAN defines two joining procedures for end-devices: OTAA and ABP.
OTAA requires DevEUI, the AppEUI, and an AppKey. An end-device must follow this procedure every time it joins a new network or loses the session key information. Devices perform a join-procedure with the network, during which a dynamic DevAddr is assigned.
The join procedure via ABP directly connects the end devices to the specified network without initiating a join request and acceptance procedure. The device address (DevAddr), NwkSKey, and AppSKey are defined directly and stored in the end device.
For more details: LoRaWAN Security Whitepaper